For the enterprise worldAdvantages of the Premium
offer
For companies that cannot compromise: the WIIT Premium offer is dedicated to organizations that, due to their size, complexity and characterization (such as, for example, listed companies), need enterprise-level IT security tools universally recognized by analysts in the field of Cyber Security.
Specifically, the Premium offer adds to the classic Managed Security Services the analysis of information flows of client companies with the possibility to enrich the information with Threat Intelligence tools and the consequent possibility to obtain valuable insights on possible attack vectors and indicators of compromise (IOC).
The service is provided through resources highly specialized in the field of Cyber Security, tools and platforms SIEM (Security Information and Event Management) with features of multi-tenancy and User Behaviour analytics.


SME-friendlyThe flexibility of the Smart offer
With the Smart offer, WIIT guarantees any type of company – even those of a smaller size – access to advanced Cyber Security services and tools. The key word is flexibility: thanks also to advantageous contractual conditions, clients can take advantage of a real SOC on demand provided by WIIT proprietary data centers.
The VPN connection to customer infrastructures makes it easy to monitor abnormal events and incidents occurring on IT infrastructures.
Service AggregatorThe functionality
of the SOCaaS
As-a-Service approachManaged Cyber Security services
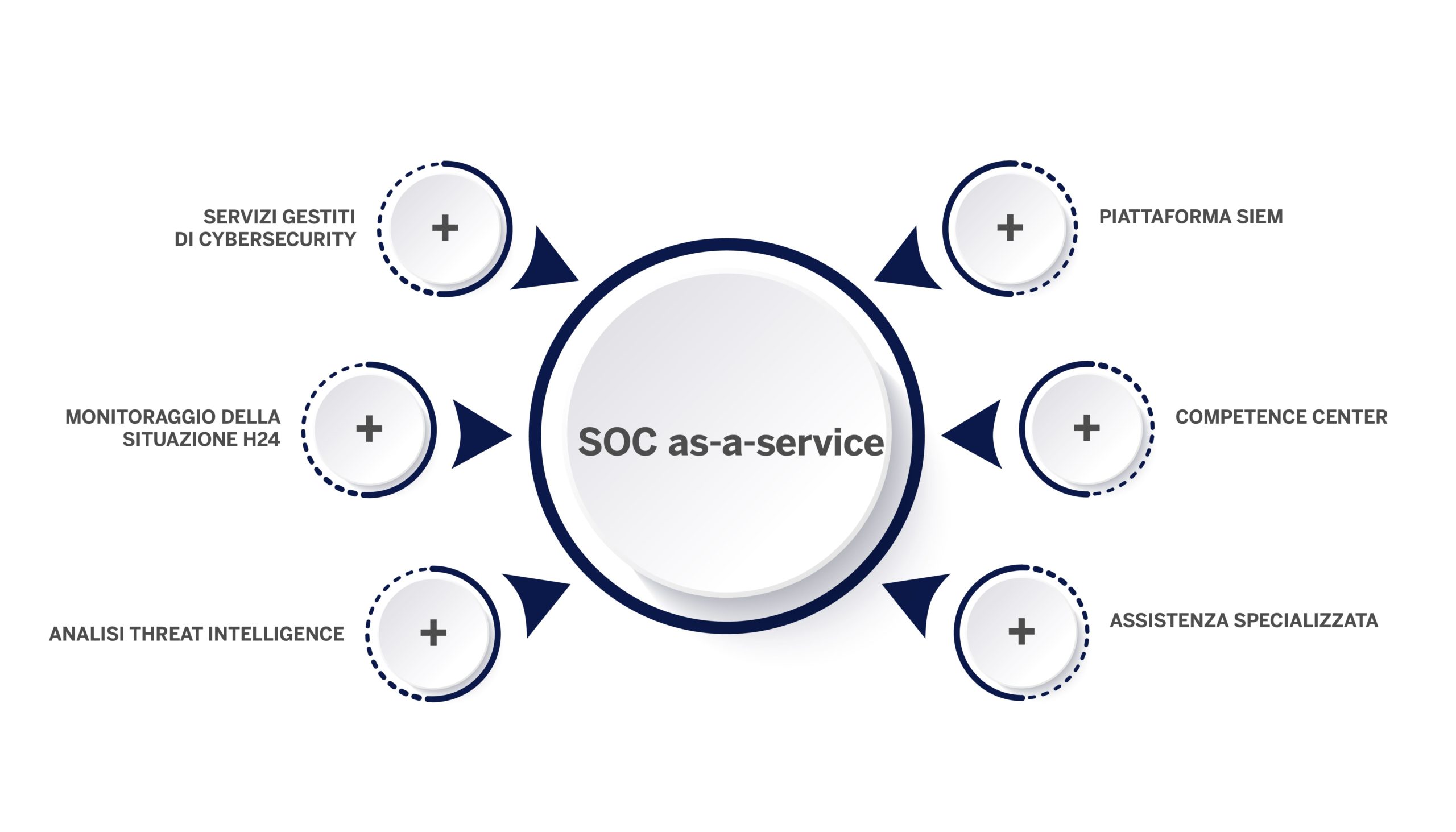
The core of the WIIT Cyber Security offer revolves around Managed Security Services. We are therefore talking about a portfolio of services managed remotely by specialized teams.
Considering that this is a constantly evolving subject, the ability to access pre-configured tools is a guarantee for all companies whose core business is not IT management. Thanks to the cloud, platforms and solutions also update and evolve without the end user having to worry about anything.

SOC as-a-Service

H24 Cyber Security
monitoring
Thanks to the skills and professionalism of the Group, an integral part of the WIIT proposition is constituted by corporate Cyber Security monitoring services: a spotlight, 24 hours a day, seven days a week, on anomalous events generated by IT systems and infrastructures.
Threat Intelligence Analysis
Threat intelligence flows allow you to analyze the inputs coming from the outside world to better understand – and therefore prevent – the dynamics with which attacks occur, regardless of the channel used.


The SIEM platform
With Security Information and Event Management (SIEM) solutions, WIIT SOCaaS accesses capabilities for analysis, aggregation and correlation of logs received from data sources. Through innovative SIEM solutions it is possible to analyze “user behaviour” and identify abnormal behaviours in order to activate timely actions to counter cyber attacks.
The SOCaaS service
Threats are intercepted by an organization characterized by: Tier 1, Tier 2 and Competence Center: Tier 1 performs an analysis of anomalous events not yet classified as incidents, categorizes them and sends the reports to Tier 2, which activates, if necessary, detailed analyses and decides on the actions to take. The Competence Center has vertical expertise on services provided and security solutions used or monitored by the Security Operations Center.


Count on expert assistance
Companies that choose the Security Managed Services offered by WIIT can also count on a highly specialized assistance service, able to face and solve specific problems focused on the specific needs of the client.
The WIIT Security index
Plant & Industrial Cybersecurity tool management activities are also grafted onto the WIIT Security Index, which includes:
178Analyzed variables
5depth levels
25weighted coefficients
100overall score points
5subscore by category
Vertical competencies for specific needs
The competence centers made available by WIIT are teams that the group has developed over the years through the implementation of projects in sectors with certified professionalism:
























